What is Elliptic Curve Cryptography (ECC)
Nicole BrownShare
Elliptic Curve Cryptography (ECC) represents one of the most significant advancements in public key cryptography of the last few decades.
This sophisticated mathematical approach to encryption has become increasingly important in modern SSL Certificate security, offering superior strength with shorter key lengths compared to traditional RSA encryption.
Understanding ECC Fundamentals
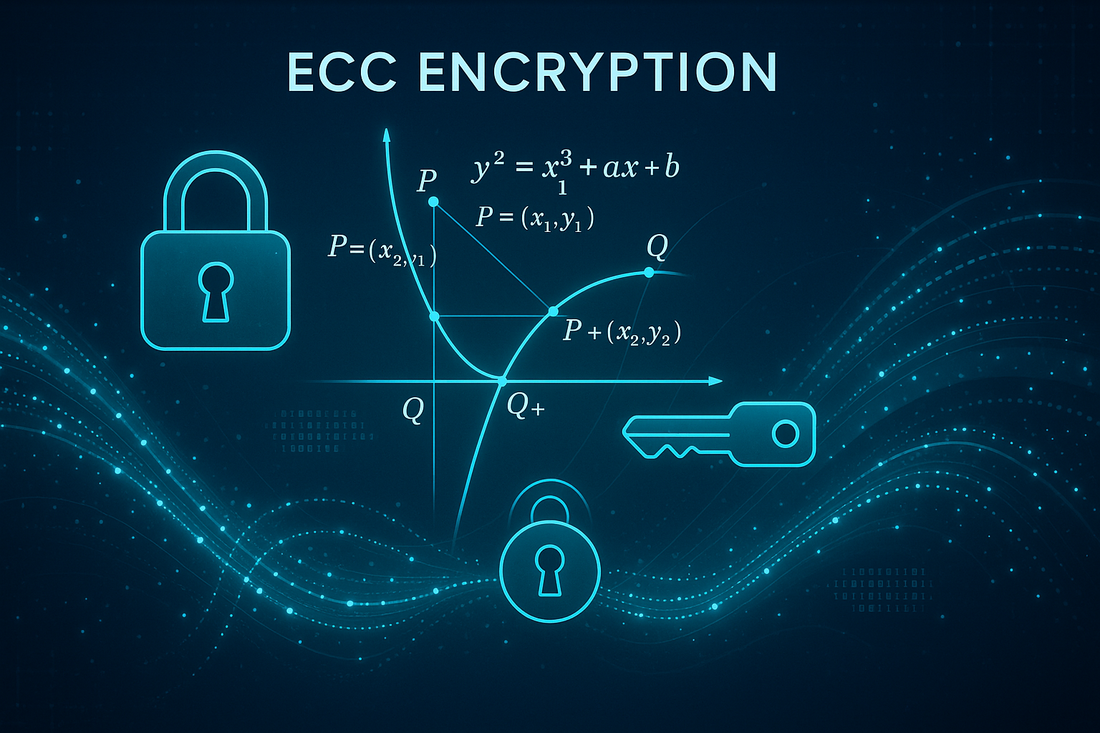
ECC relies on the algebraic structure of elliptic curves over finite fields to create cryptographic keys.
The mathematical complexity behind ECC makes it exceptionally difficult to break, even with advanced computational power. This makes ECC-based SSL Certificates particularly attractive for organizations seeking robust security solutions.
The fundamental principle of ECC centers around the difficulty of solving the elliptic curve discrete logarithm problem.
Unlike traditional RSA encryption that depends on factoring large prime numbers, ECC leverages the unique properties of elliptic curves to generate secure keys that are significantly shorter yet provide equivalent security levels.
ECC Benefits for SSL Certificates
Modern SSL Certificates utilizing ECC offer substantial advantages over traditional RSA-based SSL Certificates.
The most notable benefit is the ability to achieve the same level of security with much smaller key sizes. For example, a 256-bit ECC key provides comparable security to a 3072-bit RSA key.
The reduced key size of ECC-based SSL Certificates translates to faster processing times and lower resource consumption. This efficiency becomes particularly important in environments where computational resources are limited, such as mobile devices and Internet of Things (IoT) applications.
Certificate Authorities like Trustico® recognize the growing importance of ECC in modern cryptographic systems.
ECC-based SSL Certificates deliver optimal performance while maintaining the highest security standards required for protecting sensitive data transmission.
Technical Implementation and Compatibility
Implementing ECC-based SSL Certificates requires careful consideration of server configurations and client support.
Modern web servers and browsers widely support ECC, but compatibility must be verified across all intended platforms. The most commonly used curves in SSL Certificate implementations include prime256v1 and secp384r1.
During the Certificate Signing Request (CSR) generation process, administrators must specify ECC as the desired key type.
The resulting SSL Certificate will incorporate the ECC public key, enabling secure communication between servers and clients using elliptic curve-based encryption.
Future of ECC in SSL Certificate Security
As quantum computing continues to evolve, ECC positions itself as a crucial component of post-quantum cryptography strategies.
The inherent strength and efficiency of ECC make it well-suited for emerging security challenges, including the need for stronger encryption in mobile and IoT environments.
Industry experts predict increased adoption of ECC-based SSL Certificates as organizations prioritize both security and performance.
The shorter key lengths and robust encryption capabilities make ECC an ideal choice for modern digital security requirements.
Certificate Authorities continue to enhance their ECC offerings, ensuring compatibility with evolving security standards and protocols.
This ongoing development ensures that ECC-based SSL Certificates remain at the forefront of cryptographic security solutions.
Performance Considerations
When deploying ECC-based SSL Certificates, organizations experience significant performance improvements in their secure communications.
The reduced computational overhead results in faster SSL Certificate/TLS handshakes, lower CPU utilization, and improved battery life on mobile devices.
These performance benefits become particularly apparent in high-traffic environments where servers must handle numerous simultaneous SSL Certificate connections.
The efficiency of ECC allows for better scalability and reduced infrastructure requirements while maintaining superior security standards.



